Herramientas para hackear wireless

Suele suceder muy a menudo cuando tenemos una laptop, que encontramos muchas redes WIFI disponibles, pero todas solicitan una clave para poder conectarnos.
Aqui les presento la lista mas completa de toolkits, frameworks, herramientas con las que podemos realizar pruebas de penetración WIFI y conseguir el tan ansiado acceso a internet.
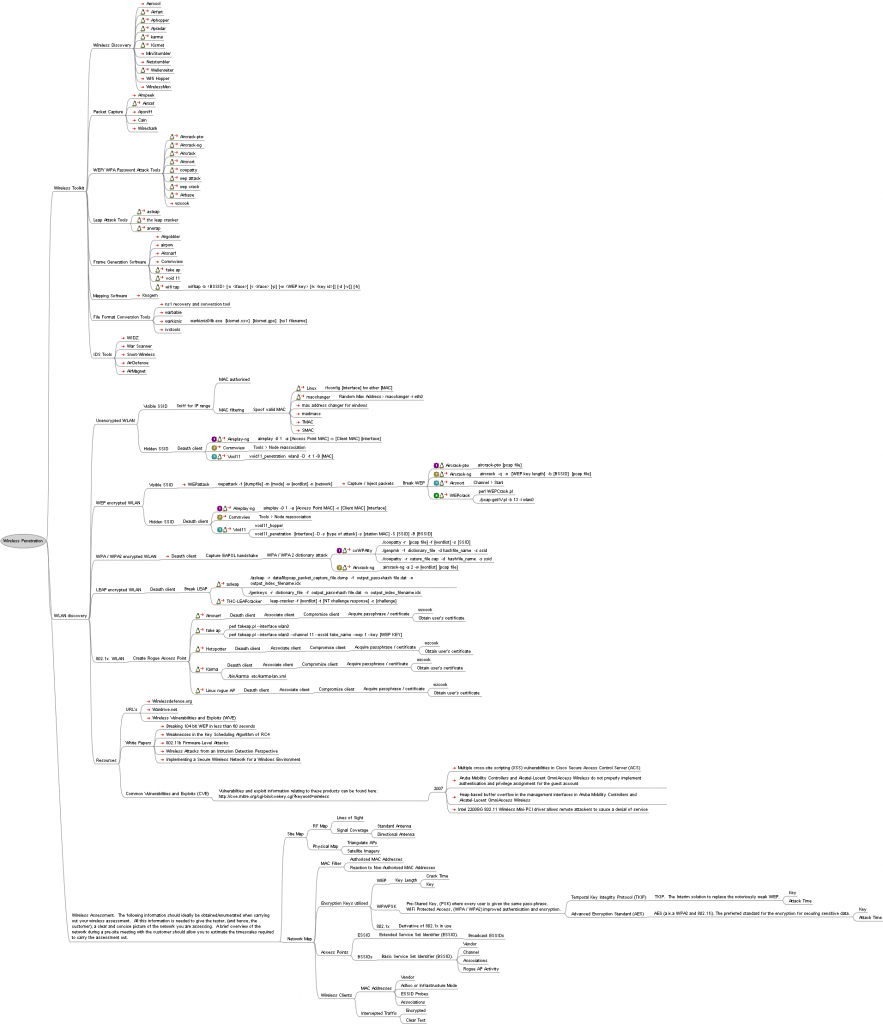
Penetración Wireless
- Wireless Toolkit
- Wireless Discovery
- Packet Capture
- WEP/WPA Password Attack Tools
- Leap Attack Tools
- Frame Generation Software
- Mapping Software
- File Format Conversion Tools
- ns1 recovery and conversion tool
- warbable
- warkizniz
- warkizniz04b.exe [kismet.csv] [kismet.gps] [ns1 filename]
- ivstools
- IDS Tools
- WLAN discovery
- Unencrypted WLAN
- Visible SSID
- Sniff for IP range
- MAC authorised
- MAC filtering
- Spoof valid MAC
- Linux
- ifconfig [interface] hw ether [MAC]
- macchanger
- Random Mac Address:- macchanger -r eth0
- mac address changer for windows
- madmacs
- TMAC
- SMAC
- Linux
- Spoof valid MAC
- Sniff for IP range
- Hidden SSID
- Deauth client
- Aireplay-ng
- aireplay -0 1 -a [Access Point MAC] -c [Client MAC] [interface]
- Commview
- Tools > Node reassociation
- Void11
- void11_penetration wlan0 -D -t 1 -B [MAC]
- Aireplay-ng
- Deauth client
- Visible SSID
- WEP encrypted WLAN
- Visible SSID
- WEPattack
- wepattack -f [dumpfile] -m [mode] -w [wordlist] -n [network]
- Capture / Inject packets
- Break WEP
- Aircrack-ptw
- aircrack-ptw [pcap file]
- Aircrack-ng
- aircrack -q -n [WEP key length] -b [BSSID] [pcap file]
- Airsnort
- Channel > Start
- WEPcrack
- perl WEPCrack.pl
- ./pcap-getIV.pl -b 13 -i wlan0
- Aircrack-ptw
- Break WEP
- Capture / Inject packets
- wepattack -f [dumpfile] -m [mode] -w [wordlist] -n [network]
- WEPattack
- Hidden SSID
- Deauth client


- Aireplay-ng
- aireplay -0 1 -a [Access Point MAC] -c [Client MAC] [interface]
- Commview
- Tools > Node reassociation
- Void11
- void11_hopper
- void11_penetration [interface] -D -s [type of attack] -s [station MAC] -S [SSID] -B [BSSID]
- Aireplay-ng
- Deauth client
- Visible SSID
- WPA/WPA2 encrypted WLAN
- Deauth client
- Capture EAPOL handshake
- WPA / WPA 2 dictionary attack
- coWPAtty
- ./cowpatty -r [pcap file] -f [wordlist] -s [SSID]
- ./genpmk -f dictionary_file -d hashfile_name -s ssid
- ./cowpatty -r cature_file.cap -d hashfile_name -s ssid
- Aircrack-ng
- Aircrack-ng -a 2 -w [wordlist] [pcap file]
- coWPAtty
- WPA / WPA 2 dictionary attack
- Capture EAPOL handshake
- Deauth client
- LEAP encrypted WLAN
- Deauth client
- Break LEAP
- asleap
- ./asleap -r data/libpcap_packet_capture_file.dump -f output_pass+hash file.dat -n output_index_filename.idx
- ./genkeys -r dictionary_file -f output_pass+hash file.dat -n output_index_filename.idx
- THC-LEAPcracker
- leap-cracker -f [wordlist] -t [NT challenge response] -c [challenge]
- asleap
- Break LEAP
- Deauth client
- 802.1x WLAN
- Create Rogue Access Point
- Airsnarf
- Deauth client
- Associate client
- Compromise client
- Acquire passphrase / certificate
- wzcook
- Obtain user’s certificate
- Acquire passphrase / certificate
- Compromise client
- Associate client
- Deauth client
- fake ap
- perl fakeap.pl –interface wlan0
- perl fakeap.pl –interface wlan0 –channel 11 –essid fake_name –wep 1 –key [WEP KEY]
- Hotspotter
- Deauth client
- Associate client
- Compromise client
- Acquire passphrase / certificate
- wzcook
- Obtain user’s certificate
- Acquire passphrase / certificate
- Compromise client
- Associate client
- Deauth client
- Karma
- Deauth client
- Associate client
- Compromise client
- Acquire passphrase / certificate
- wzcook
- Obtain user’s certificate
- Acquire passphrase / certificate
- Compromise client
- Associate client
- ./bin/karma etc/karma-lan.xml
- Deauth client
- Linux rogue AP
- Deauth client
- Associate client
- Compromise client
- Acquire passphrase / certificate
- wzcook
- Obtain user’s certificate
- Acquire passphrase / certificate
- Compromise client
- Associate client
- Deauth client
- Airsnarf
- Create Rogue Access Point
- Resources
- URL’s
- White Papers
- Common Vulnerabilities and Exploits (CVE)
- Vulnerabilties and exploit information relating to these products can be found here: http://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=wireless
- 2007
- Multiple cross-site scripting (XSS) vulnerabilities in Cisco Secure Access Control Server (ACS)
- Aruba Mobility Controllers and Alcatel-Lucent OmniAccess Wireless do not properly implement authentication and privilege assignment for the guest account
- Heap-based buffer overflow in the management interfaces in Aruba Mobility Controllers and Alcatel-Lucent OmniAccess Wireless
- Intel 2200BG 802.11 Wireless Mini-PCI driver allows remote attackers to cause a denial of service
- 2007
- Vulnerabilties and exploit information relating to these products can be found here: http://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=wireless
- Unencrypted WLAN
- Wireless Assessment. The following information should ideally be obtained/enumerated when carrying out your wireless assessment. All this information is needed to give the tester, (and hence, the customer), a clear and concise picture of the network you are assessing. A brief overview of the network during a pre-site meeting with the customer should allow you to estimate the timescales required to carry the assessment out.
- Site Map
- RF Map
- Lines of Sight
- Signal Coverage
- Standard Antenna
- Directional Antenna
- Physical Map
- Triangulate APs
- Satellite Imagery
- RF Map
- Network Map
- MAC Filter
- Authorised MAC Addresses
- Reaction to Non-Authorised MAC Addresses
- Encryption Keys utilised
- WEP
- Key Length
- Crack Time
- Key
- Key Length
- WPA/PSK
- Pre-Shared Key, (PSK) where every user is given the same pass-phrase.
WiFi Protected Access, (WPA / WPA2) improved authentication and encryption.- Temporal Key Integrity Protocol (TKIP)
- TKIP. The Interim solution to replace the notoriously weak WEP.
- Key
- Attack Time
- TKIP. The Interim solution to replace the notoriously weak WEP.
- Advanced Encryption Standard (AES)
- AES (a.k.a WPA2 and 802.11i). The preferred standard for the encryption for securing sensitive data.
- Key
- Attack Time
- AES (a.k.a WPA2 and 802.11i). The preferred standard for the encryption for securing sensitive data.
- Temporal Key Integrity Protocol (TKIP)
- Pre-Shared Key, (PSK) where every user is given the same pass-phrase.
- 802.1x
- Derivative of 802.1x in use
- WEP
- Access Points
- ESSID
- Extended Service Set Identifier (ESSID).
- Broadcast ESSIDs
- Extended Service Set Identifier (ESSID).
- BSSIDs
- Basic Service Set Identifier (BSSID).
- Vendor
- Channel
- Associations
- Rogue AP Activity
- Basic Service Set Identifier (BSSID).
- ESSID
- Wireless Clients
- MAC Addresses
- Vendor
- Adhoc or Infrastructure Mode
- ESSID Probes
- Associations
- Intercepted Traffic
- Encrypted
- Clear Text
- MAC Addresses
- MAC Filter
- Site Map